Argo CD : Setup with EKS
what is GitOps?
GitOps is a bunch of best practices where the whole code conveyance process is controlled through Git, including framework and application definition as code and robotization to finish updates and rollbacks.
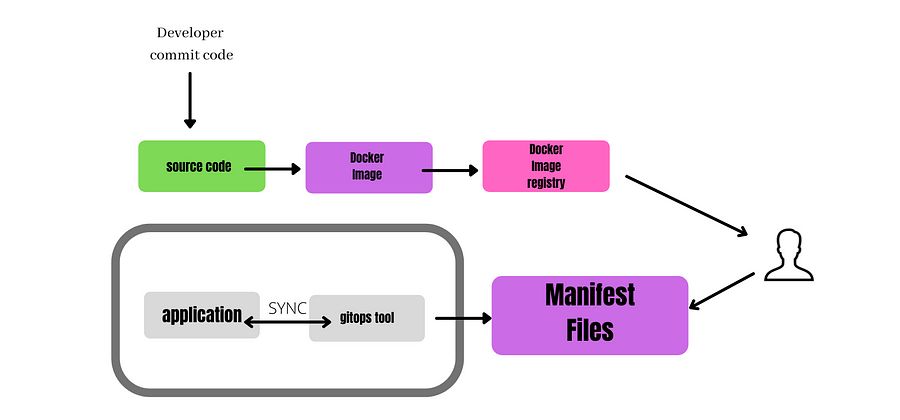
GitOps FLOW
A few Pros of GitOps:
Quicker organizations
More secure organizations
More straightforward rollbacks
Clear evaluating
Better discernibility
Disposing of arrangement float
why Argo CD?
Argo CD implements all features of GitOps. Argo CD contains a coordinated UI that shows you the design of your application just as the synchronization status (regardless of whether the bunch matches Git anytime).
Argo CD is mainly used for deploying and managing applications on the K8S cluster.
Features:
sync functionality (manual & auto)
declarative configuration
INSTALLATION
Before starting hope we have already eks cluster running. Use below YAML about how to create eks cluster using eksctl utility.
---
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: myDemo
region: ap-south-1
version: '1.28'
addons:
- name: vpc-cni
attachPolicyARNs:
- arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy
- name: coredns
version: latest
- name: kube-proxy
version: latest
- name: aws-ebs-csi-driver
wellKnownPolicies:
ebsCSIController: true
- name: eks-pod-identity-agent
tags:
team: eks
iam:
withOIDC: true
podIdentityAssociations:
- namespace: default
serviceAccountName: s3-reader
roleARN: arn:aws:iam::xxxxxx:role/PodIdentityTestDemo
accessConfig:
bootstrapClusterCreatorAdminPermissions: false
authenticationMode: API_AND_CONFIG_MAP
accessEntries:
- principalARN: arn:aws:iam::xxxxxxx:user/test
accessPolicies:
- policyARN: arn:aws:eks::aws:cluster-access-policy/AmazonEKSClusterAdminPolicy
accessScope:
type: cluster
nodeGroups:
- name: myWorkerNodeGroup1
instanceType: m5.large
desiredCapacity: 1
volumeSize: 30
volumeType: gp3
volumeEncrypted: true
amiFamily: Ubuntu2004
ssh:
publicKeyPath: ~/.ssh/id_rsa.pub
- name: myWorkerNodeGroup2
instanceType: m5.large
desiredCapacity: 1
amiFamily: Ubuntu2004
ssh: # import default public key (~/.ssh/id_rsa.pub)
allow: true
cloudWatch:
clusterLogging:
enableTypes: ["audit", "authenticator", "controllerManager"]
# all supported types: "api", "audit", "authenticator", "controllerManager", "scheduler"
# supported special values: "*" and "all"
logRetentionInDays: 14
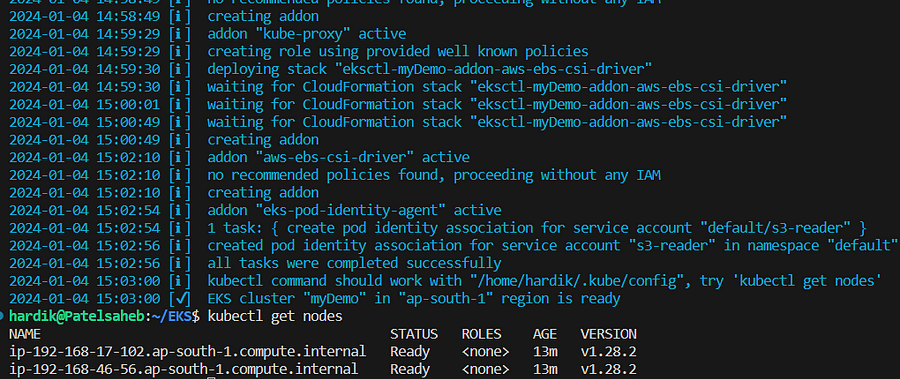
create cluster using below command ,
eksctl create cluster -f myeks.yaml
Install ArgoCD
We are going to create custom helm chart ( Umbrella Chart ) for ArgoCD installation on our EKS cluster.
As we knew Argo Project doesn’t provide Official Helm Chart. So we are going to create custom chart. It will pull original chart and after that we will overrides default values.
follow below steps,
mkdir -p charts/argo-cd
add Chart.yaml file in it with below content,
apiVersion: v2
name: argo-cd
version: 1.0.0
dependencies:
- name: argo-cd
version: 5.46.8
repository: https://argoproj.github.io/argo-helm
Next, create a values.yaml file for our chart,
argo-cd:
dex:
enabled: false
notifications:
enabled: false
applicationSet:
enabled: false
server:
service:
type: LoadBalancer
extraArgs:
- --insecure
All available options for the Argo CD Helm chart can be found in the values.yaml file.
Now, we need to generate Helm chart lock file. When we tried to install it checks for lock file for such dependency and download it.
Lets add repo,
helm repo add argo-cd https://argoproj.github.io/argo-helm
helm dep update charts/argo-cd/
above commands will Chart.lock and charts/argo-cd-<version>.tgz files
lets create one git repo and push all in it.
echo "charts/**/charts" >> .gitignore
git add charts/argo-cd
git commit -m 'add argo-cd chart'
git push
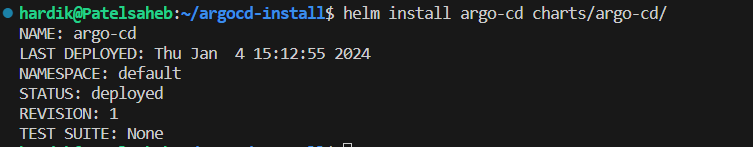
Now, we will install this chart.
helm install argo-cd charts/argo-cd/
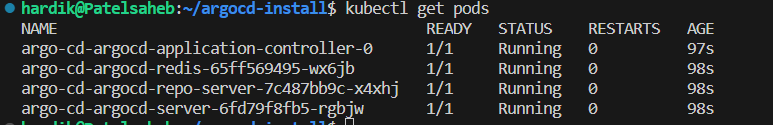
Verify now,
kubectl get pods
Note: In this demo, I used a load balancer service type
kubectl patch svc argo-cd-argocd-server -p '{"spec": {"type": "LoadBalancer"}}'
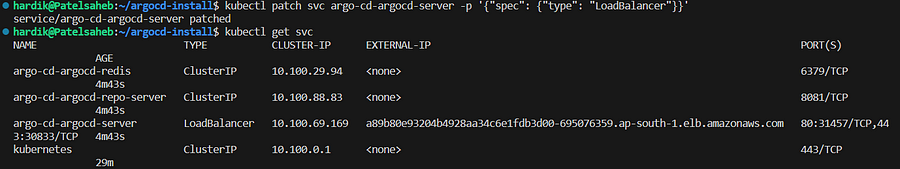
Now you will get external ALB URL. Copy that and paste it in browser,
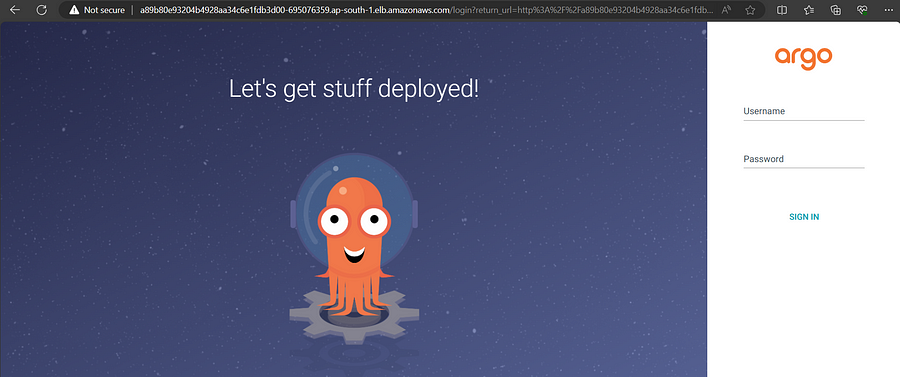
Next, get the password of default user,
kubectl get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d
After successful login,
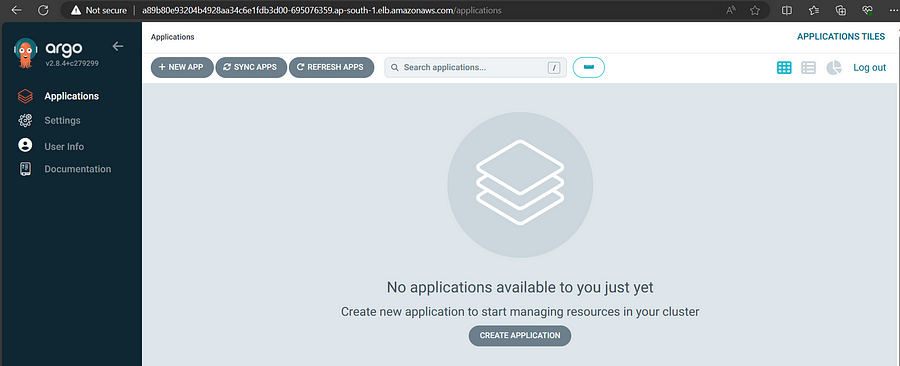
Generally, If we want to add an application to Argo CD, need to add an Application resource in Kubernetes cluster. In this tutorial, we'll focus on creating applications that use Helm charts.
The easy to go method is using the manifest file and deploy it through kubectl CLI. This manual way is errorless and repetitive task.
ArgoCD have better way to manage this. We are going to do automation with the concept of app of apps pattern.
Lets create baseline app,
mkdir -p charts/baseline/templates
touch charts/baseline/values.yaml
charts/baseline/Chart.yaml
apiVersion: v2
name: baseline
version: 1.0.0
charts/baseline/template/baseline.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: baseline-app
finalizers:
- resources-finalizer.argocd.argoproj.io
spec:
project: default
source:
repoURL: https://github.com/hardikpatel29/argocd-install.git
path: charts/baseline/
targetRevision: HEAD
destination:
server: https://kubernetes.default.svc
namespace: default
syncPolicy:
automated:
selfHeal: true
push files in git
git add charts/baseline
git commit -m 'added baseline apps'
git push
deploy it ,
helm template baseline/ | kubectl apply -f -
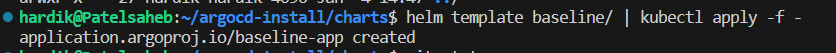
As we knew that we have deploy argocd using helm chart manually. So if any changes we made in such case we need to deploy it manually again.
So to manage this we can use ArgoCD controller that monitor changes in manifest files in our git repo and apply it asynchronously.
To achieve this we are going to create template yaml as below,
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: argo-cd
finalizers:
- resources-finalizer.argocd.argoproj.io
spec:
project: default
source:
repoURL: https://github.com/hardikpatel29/argocd-install.git
path: charts/argo-cd
targetRevision: HEAD
destination:
server: https://kubernetes.default.svc
namespace: default
syncPolicy:
automated:
selfHeal: false
than push this files in git and we are done.
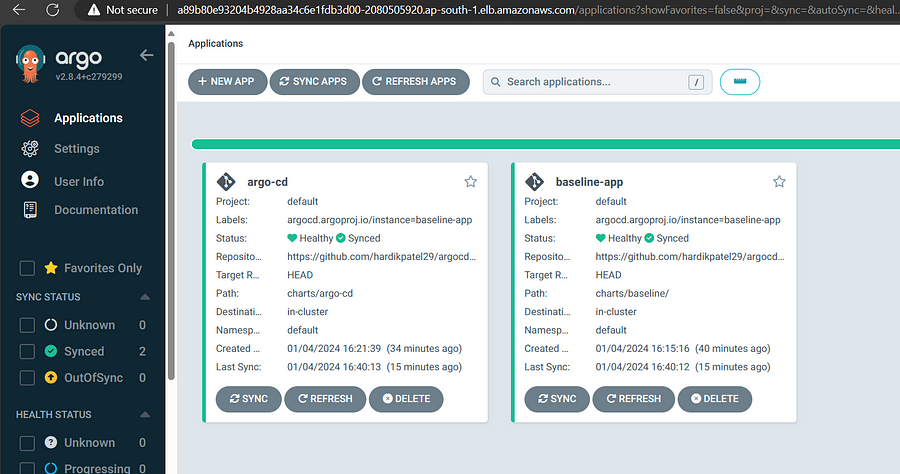
If you want to check directory structure please take look on link.
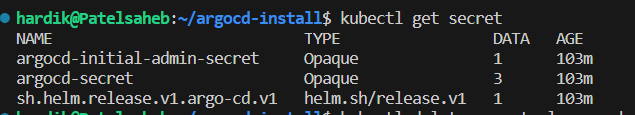
Lets check secret created by Helm,
kubectl get secret
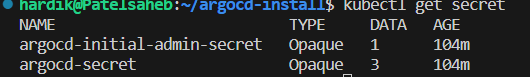
Now we are going to delete secret created by helm chart installation,
kubectl delete secret -l owner=helm,name=argo-cd
Conclusion
Deploying ArgoCD on Amazon EKS using Helm presents a streamlined approach to managing Kubernetes applications and configurations. By harnessing the power of ArgoCD’s continuous delivery capabilities and the simplicity of Helm charts, this setup offers a robust and efficient way to automate deployment workflows.
Ultimately, the integration of ArgoCD and Helm on Amazon EKS lays the groundwork for a scalable, automated, and resilient infrastructure, propelling your deployment processes towards efficiency and success in your Kubernetes orchestration.
