ArgoCD : Configure Projects & Applications
Introduction
Welcome to our comprehensive guide on setting up and maximizing the potential of ArgoCD! If you’re looking to streamline your project management, optimize role assignments, establish efficient application setups, you’re in the right place. Argo CD's power lies in its ability to orchestrate these vital components, whether you’re working with public or private repositories. Let’s dive into the key steps and considerations for a successful ArgoCD setup.
Before starting please follow below link to setup Argo CD cluster.
Project & Role:
Projects in ArgoCD serve as organizational units to group applications, providing a logical separation for managing access control, settings, and resources.
Mostly useful where multiple teams operation ArgoCD cluster.
allow certain git repos
restrict where to deploy app
limit to resource deployment like statefulset,deployments
Roles in ArgoCD define permissions and access levels for users or groups within projects, allowing fine-grained control over who can perform specific actions.
With roles we can restrict any CI system to use particular project applications.
Lets create project and roles and create sample application in that,
lets view project first,
kubectl get appproject -o yaml
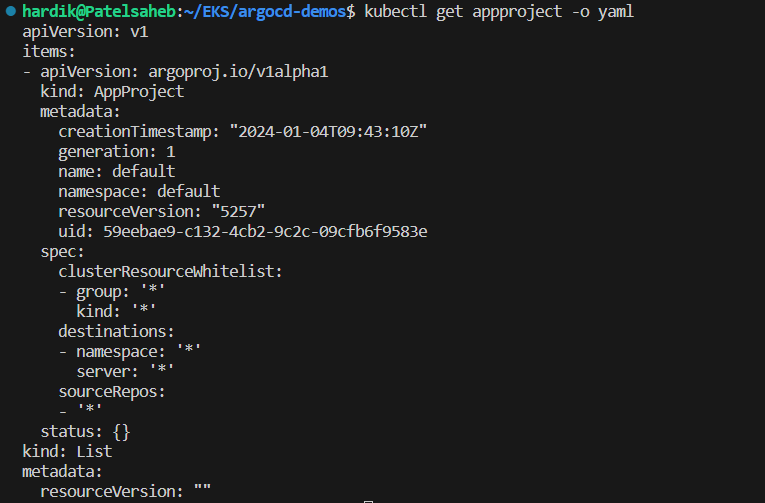
above ss shows that ArgoCD default project allow all repos and any destination cluster.
project.yaml,
apiVersion: argoproj.io/v1alpha1
kind: AppProject
metadata:
name: demo-project
namespace: default
spec:
description: MydemoProject
sourceRepos:
- '*'
destinations:
- namespace: '*'
server: '*'
clusterResourceWhitelist:
- group: '*'
kind: '*'
namespaceResourceWhitelist:
- group: '*'
kind: '*'
create it using kubectl command,
kubectl apply -f project.yaml
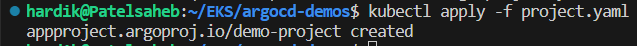
To verify in GUI, go into setting section and click on project,
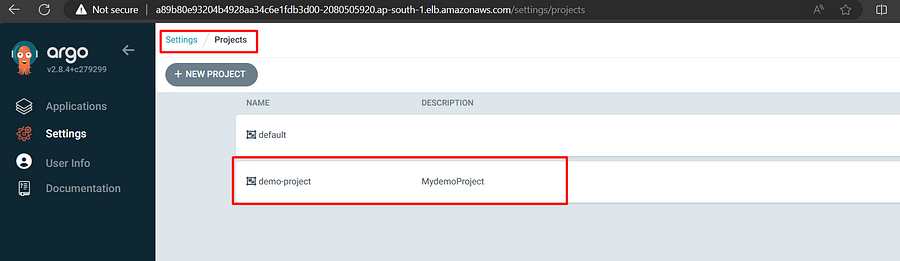
To create project role, first we need to create token and without token role will be not useful. additionally, generated token we cant store in ArgoCD.
we can leverage token by passing argument like — auth-token in cli or we can use env variable like ARGOCD_AUTH_TOKEN.
project-role.yaml,
apiVersion: argoproj.io/v1alpha1
kind: AppProject
metadata:
name: project-role
namespace: default
spec:
description: project-role
sourceRepos:
- '*'
destinations:
- namespace: '*'
server: '*'
clusterResourceWhitelist:
- group: '*'
kind: '*'
namespaceResourceWhitelist:
- group: '*'
kind: '*'
roles:
- name: myrole
description: my project role
policies:
- p, proj:project-role:myrole, applications, sync, project-role/*, allow
as per above yaml, roles section define the role name, permission at project level.
kubectl apply -f project-role.yaml
now lets first login ArgoCD server from cli,
argocd login xxxxx
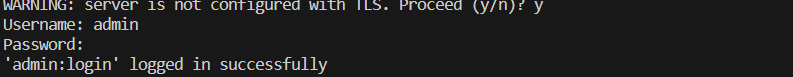
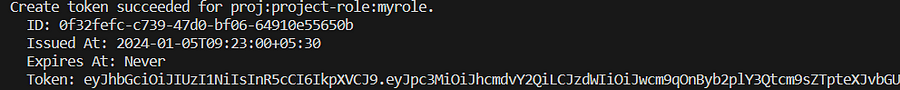
Lets create token first,
argocd proj role create-token project-role myrole
get something like this,
lets access app list,
argocd app list
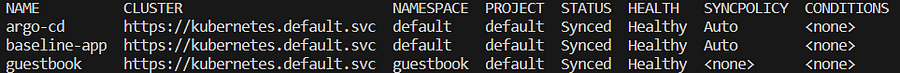
lets delete app to check our roles permission,
argocd app delete guestbook --auth-token eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJwcm9qOnByb2plY3Qtcm9sZTpteXJvbGUiLCJuYmYiOjE3MDQ0
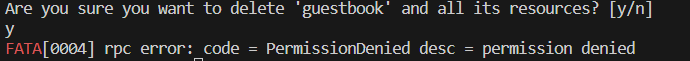
It’s say permission denied. As we given permission only sync while creation of role. So its working.
roles:
- name: myrole
description: my project role
policies:
- p, proj:project-role:myrole, applications, sync, project-role/*, allow
Applications:
In essence, an ArgoCD application acts as the blueprint that drives the deployment and maintenance of your application or microservice, allowing for automated and efficient management of your infrastructure.
Application is Kubernetes resources object that represent application instance in environment.
There is 2 important information to define application yaml,
source: reference to git repo desired state
destination: target cluster and namespace
We have below options to for creation of applications,
Declarative Approach (Recommended)
GUI
CLI
ArgoCD supports different ways to define applications in how you describe and manage your deployments. Here are common ways to define applications:
Helm Chart
Kustomize
Ksonnet(Jsonnet)
Custom Resource Definitions (CRDs)
Each of these methods offers distinct advantages and caters to different preferences or requirements when it comes to defining and managing applications within ArgoCD. The choice often depends on factors like familiarity, existing infrastructure, complexity of deployments, and specific needs of the project.
application yaml ,
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: guestbook
namespace: default
spec:
destination:
namespace: guestbook
server: "https://kubernetes.default.svc"
project: default
source:
path: guestbook
repoURL: "https://github.com/hardikpatel29/argocd-examples.git"
targetRevision: master
syncPolicy:
syncOptions:
- CreateNamespace=true
Here I am considering default namespace for this demo. Lets deploy it on our eks cluster,
kubectl apply -f guestbook.yaml
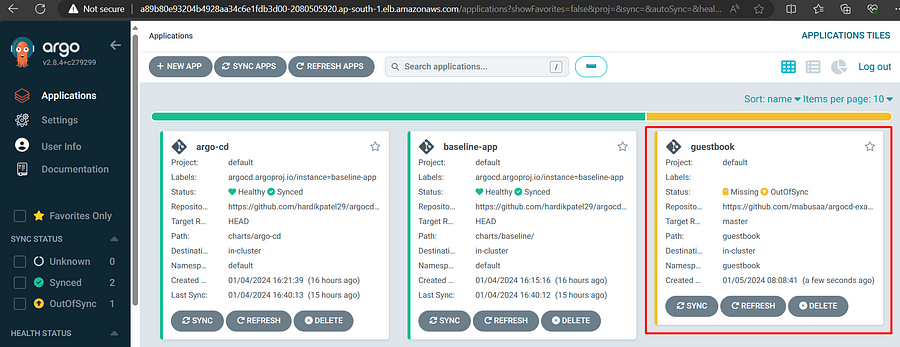
As we can see that its deployed but showing outofSync. Lets access UI and make it sync.
After that its look like,
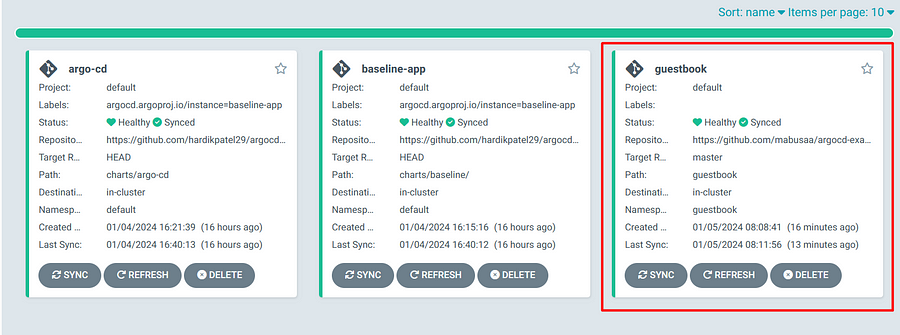
Conclusion
ArgoCD offers the flexibility and functionality to accommodate diverse setups, empowering teams to efficiently deploy and manage applications across various environments. By leveraging Argo CD's capabilities and tailoring its configurations to your specific needs, you pave the way for smoother, more efficient development cycles and operations. Embrace Argo CD's potential to optimize your project management and accelerate your deployment processes.
