Enhancing Security and Streamlining Access: Exploring EKS Pod Identity

In the ever-evolving landscape of cloud computing and container orchestration, Amazon EKS (Elastic Kubernetes Service) stands tall as a reliable and scalable solution. Recently, EKS introduced a groundbreaking feature that promises to revolutionize security and access management within Kubernetes clusters: Pod Identity.
Pod Identity introduces a new paradigm by enabling Kubernetes pods to directly assume AWS IAM (Identity and Access Management) roles. This capability facilitates a seamless and secure interaction between applications running in EKS clusters and various AWS services.
With Pod Identity, its easy to configure and automate granting permissions to K8S identities. As a cluster admin, we didnt need to switch between eks console and IAM console. Initially there was only way to achieve this was to manually write IAM creds to our k8s cluster.
EKS Pod Identity Restrictions
update to latest aws cli
Worker nodes must be Linux ec2 instance only
only available with EKS only. not supported for cluster which we created manually
EKS anywhere is not supported
Step1:
Lets create custom IAM policy that have access to s3 bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "s3:GetObject",
"Effect": "Allow",
"Resource": "arn:aws:s3:::myekspodtesting/*",
"Sid": "PodIdentity"
}
]
}
Step2:
Create a new role name PodIdentityTestDemo with trust policy as below and attach above policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "pods.eks.amazonaws.com"
},
"Action": [
"sts:AssumeRole",
"sts:TagSession"
]
}
]
}
Step3:
Lets assume EKS cluster is already created. create a addon first.
aws eks create-addon \
--cluster-name mycluster \
--addon-name eks-pod-identity-agent \
--addon-version v1.0.0-eksbuild.1
Next Association of Pod identity Role earlier we created,
aws eks create-pod-identity-association \
--cluster-name mycluster \
--service-account s3-reader \
--role-arn arn:aws:iam::xxxxxx:role/PodIdentityTestDemo \
--namespace default
We can also create cluster using eksctl utility. yaml file as below,
---
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: myDemo
region: ap-south-1
version: '1.28'
addons:
- name: vpc-cni
attachPolicyARNs:
- arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy
- name: coredns
version: latest
- name: kube-proxy
version: latest
- name: aws-ebs-csi-driver
wellKnownPolicies:
ebsCSIController: true
- name: eks-pod-identity-agent
tags:
team: eks
iam:
withOIDC: true
podIdentityAssociations:
- namespace: default
serviceAccountName: s3-reader
roleARN: arn:aws:iam::xxxxxx:role/PodIdentityTestDemo
nodeGroups:
- name: myWorkerNodeGroup1
instanceType: m5.large
desiredCapacity: 1
volumeSize: 30
volumeType: gp3
volumeEncrypted: true
amiFamily: Ubuntu2004
ssh:
publicKeyPath: ~/.ssh/id_rsa.pub
- name: myWorkerNodeGroup2
instanceType: m5.large
desiredCapacity: 1
amiFamily: Ubuntu2004
ssh:
allow: true
cloudWatch:
clusterLogging:
enableTypes: ["audit", "authenticator", "controllerManager"]
logRetentionInDays: 14
We are done with configuration and ready for testing.
First lets verify addon daemonset,
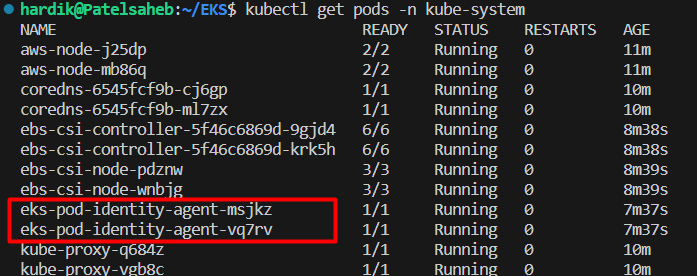
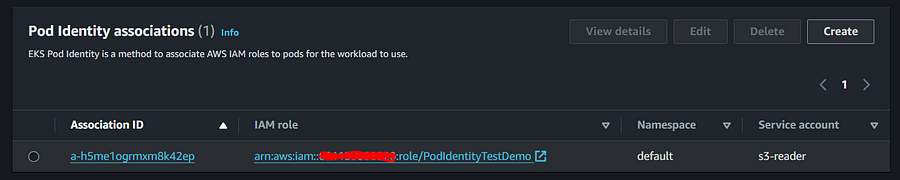
Also, we can verify through command,
aws eks list-pod-identity-associations --cluster-name myDemo --region ap-south-1
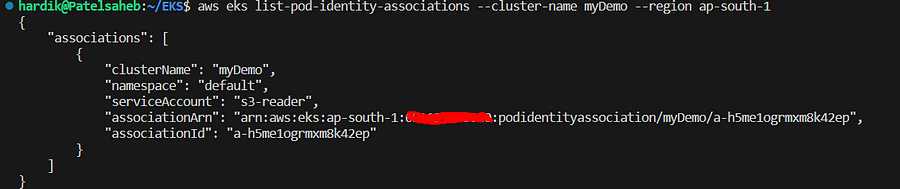
Lets launch one pod on our eks cluster, yaml is as below,
apiVersion: apps/v1
kind: Deployment
metadata:
name: s3-reader
labels:
app: s3-reader
spec:
replicas: 1
selector:
matchLabels:
app: s3-reader
template:
metadata:
labels:
app: s3-reader
spec:
serviceAccountName: s3-reader
containers:
- name: s3-reader
image: makoreactor/debug:latest
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: s3-reader
labels:
app: s3-reader
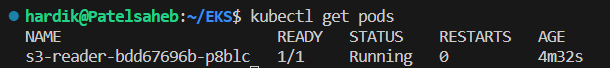
lets take shell access of pod,
kubectl exec -it s3-reader-bdd67696b-p8blc bash
SERVICE_TOKEN=`cat /var/run/secrets/pods.eks.amazonaws.com/serviceaccount/eks-pod-identity-token`
curl 169.254.170.23/v1/credentials -H "Authorization: $SERVICE_TOKEN" | jq .
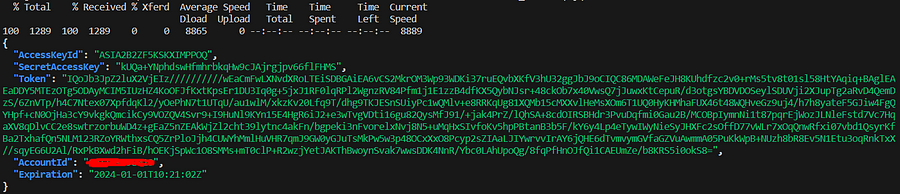
aws sts get-caller-identity
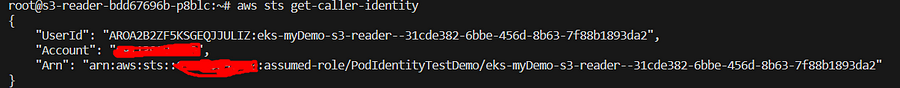
Now, we should go to access s3 bucket object,
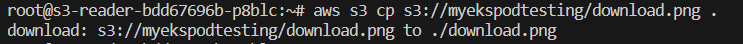
Conclusion
EKS Pod Identity feature is a new way to grant and manage permissions at pod level in a cluster.
EKS Pod Identity introduces a transformative approach to security and access management within Kubernetes clusters. Its ability to seamlessly integrate with AWS IAM roles not only fortifies security measures but also streamlines operational workflows.
As organizations prioritize robust security measures and seek streamlined access controls, EKS Pod Identity emerges as a pivotal feature, redefining the landscape of Kubernetes security and access management.
